What is MPLS Traffic Engineering (MPLS-TE)?
MPLS Traffic Engineering (MPLS-TE) is a technology that enhances the capabilities of MPLS (Multiprotocol Label Switching) to enable more granular control over traffic flow within a network. This is achieved by manipulating traffic paths to optimize resource usage, avoid congestion, and meet specific service requirements, like bandwidth guarantees or low latency.
Traffic engineering refers to the practice of optimizing the flow of network traffic in a way that ensures efficient use of network resources, avoids congestion, and achieves better overall performance. In traditional IP networks, traffic generally follows the shortest path, which can lead to suboptimal usage of network capacity and congestion. MPLS-TE allows operators to move beyond shortest-path routing by explicitly setting up paths through the network that distribute traffic more evenly.
In this lab I’m going to configure a tunnel to overrule the IGP shortest path and chose a different path.
MPLS Lab Setup
Labs download |
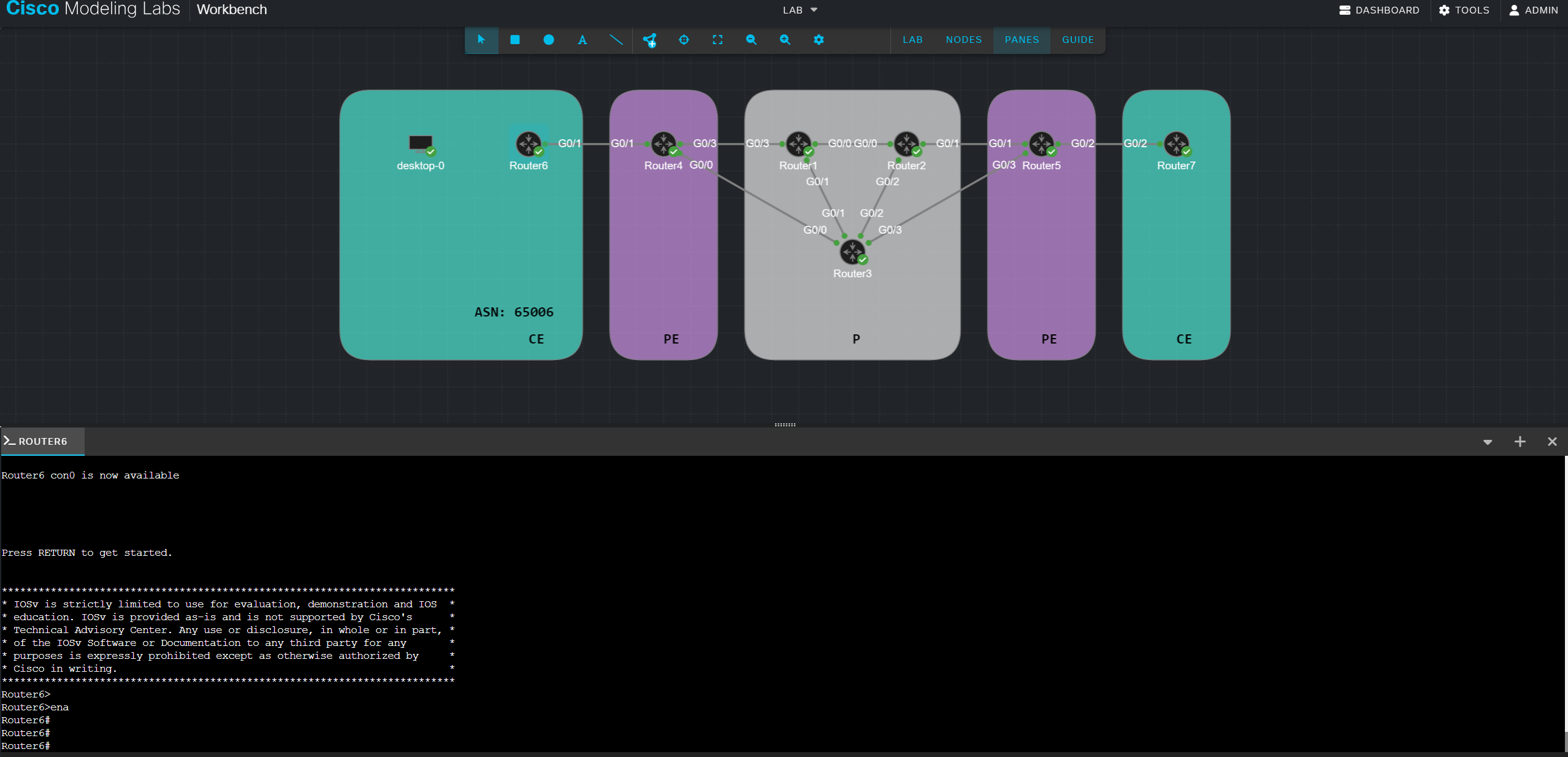
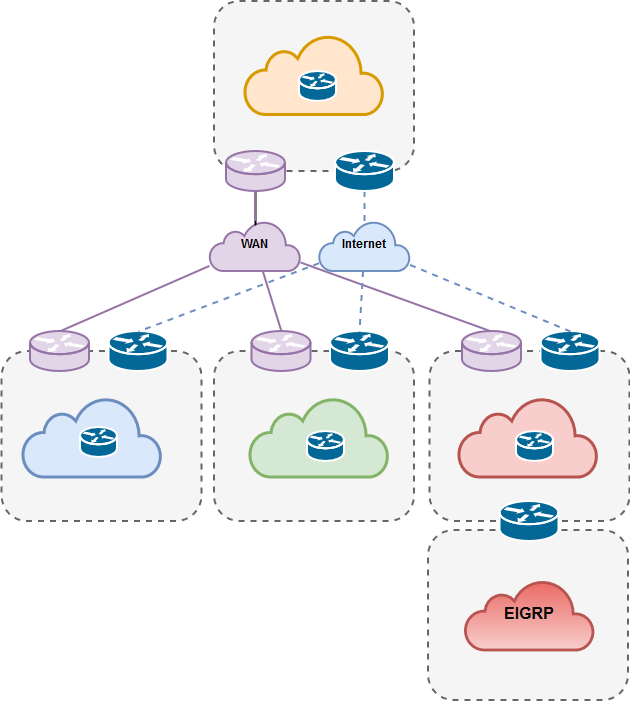
Using Cisco’s Modeling Labs (CML) I build the following MPLS lab using OSPF and LDP neighbor relationships.
- 3 x P routers (Router1, Router2, Router3)
- 2 x PE router (Router4, Router5)
- 2 x CE router (Router6, Router7)
Default Behaviour
The default traffic flow behaviour from PE Router4 towards PE Router5 will follow the IGP shortest path via P Router3. This path is one hop instead of traversing via Router1+Router2 being two hops away and double the cost.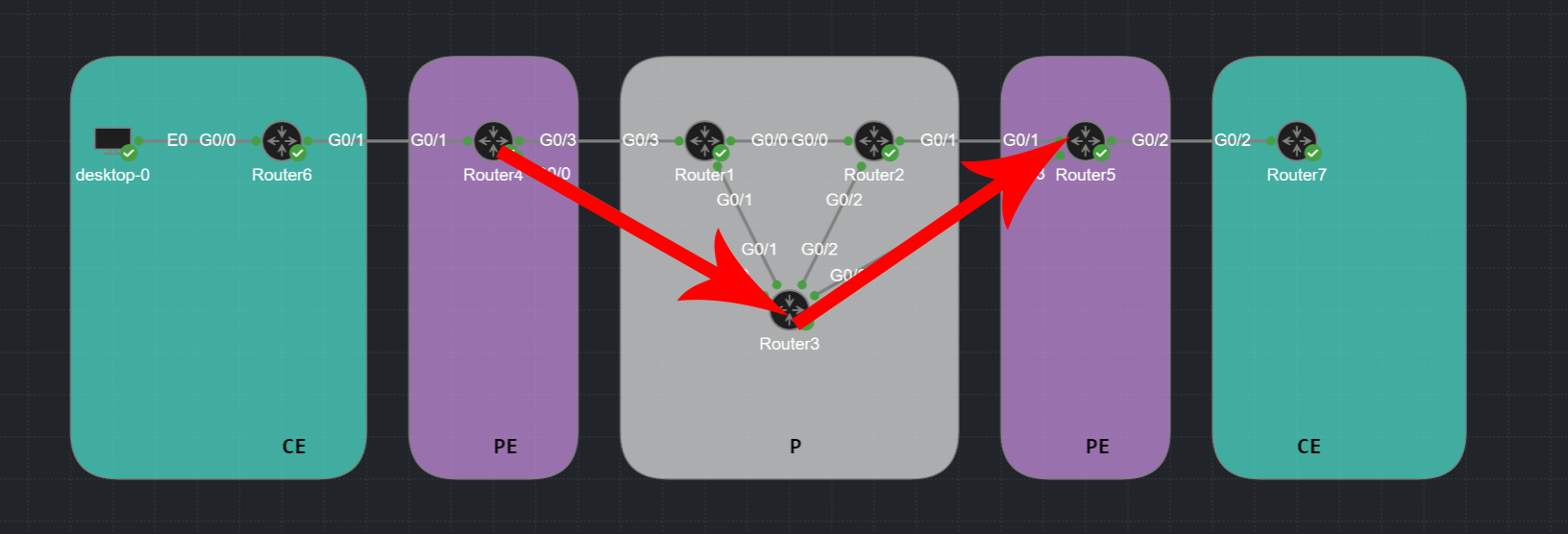
MPLS-TE
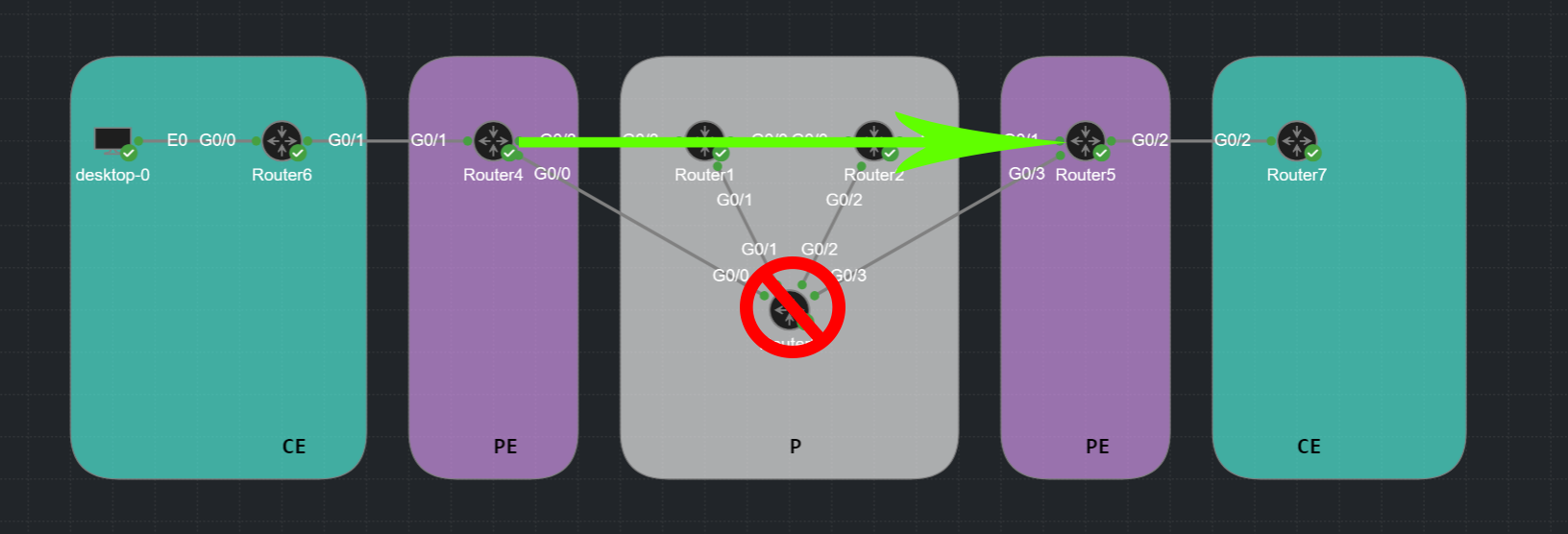
With MPLS-TE we can define a different path via Router1+Router2.
There can be many reasons why we would want to do this and many ways how we can achieve this. In this Lab I am going to enable MPLS-TE and simply exclude Router3 from our path.
| Device | Function | Loopback address | Subnets | Label Ranges |
|---|---|---|---|---|
| Router1 | P Router | 1.1.1.1/32 | Gi0/0 10.1.2.1/24 Gi0/1 10.1.3.1/24 Gi0/3 10.1.4.1/24 | 100-199 |
| Router2 | P Router | 2.2.2.2/32 | Gi0/0 10.1.2.2/24 Gi0/1 10.2.3.2/24 Gi0/3 10.2.4.2/24 | 200-299 |
| Router3 | P Router | 3.3.3.3/32 | Gi0/0 10.3.4.3/24 Gi0/1 10.1.3.3/24 Gi0/2 10.2.3.3/24 Gi0/3 10.3.5.3/24 | 300-399 |
| Router4 | PE Router | 4.4.4.4/32 | Gi0/0 10.3.4.4/24 Gi0/1 10.4.6.4/24 Gi0/3 10.1.4.4/24 | 400-499 |
| Router5 | PE Router | 5.5.5.5/32 | Gi0/1 10.1.5.5/24 Gi0/2 10.5.7.5/24 Gi0/3 10.4.5.5/24 | 500-599 |
| Router6 | CE Router | 6.6.6.6/32 | Gi0/1 10.4.6.6/24 Gi0/0 192.168.1.1/24 | – |
| Router7 | CE Router | 7.7.7.7/32 | Gi0/2 10.4.6.6/24 Gi0/0 192.168.2.1/24 | – |
IP Addressing:
The point-to-point links are configured with the following IP addressing scheme:
- “10.<Lowest Router Id>.<Highest Router Id>.<Router Id>./24.”
For example the link between Router1 and Router2 gives on Router1: 10.1.2.1/24 and on Router2: 10.1.2.2/24.
Verification on Router3 (P):
Router3#sh ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
4.4.4.4 0 FULL/ - 00:00:35 10.3.4.4 GigabitEthernet0/0
1.1.1.1 0 FULL/ - 00:00:38 10.1.3.1 GigabitEthernet0/1
2.2.2.2 0 FULL/ - 00:00:35 10.2.3.2 GigabitEthernet0/2
5.5.5.5 0 FULL/ - 00:00:33 10.3.5.5 GigabitEthernet0/3
Router3#sh mpls interfaces
Interface IP Tunnel BGP Static Operational
GigabitEthernet0/0 Yes (ldp) No No No Yes
GigabitEthernet0/1 Yes (ldp) No No No Yes
GigabitEthernet0/2 Yes (ldp) No No No Yes
GigabitEthernet0/3 Yes (ldp) No No No Yes
Router3#sh mpls ldp neighbor
Peer LDP Ident: 5.5.5.5:0; Local LDP Ident 3.3.3.3:0
TCP connection: 5.5.5.5.57381 - 3.3.3.3.646
State: Oper; Msgs sent/rcvd: 46/45; Downstream
Up time: 00:26:54
LDP discovery sources:
GigabitEthernet0/3, Src IP addr: 10.3.5.5
Addresses bound to peer LDP Ident:
10.2.5.5 5.5.5.5 10.3.5.5
Peer LDP Ident: 4.4.4.4:0; Local LDP Ident 3.3.3.3:0
TCP connection: 4.4.4.4.42087 - 3.3.3.3.646
State: Oper; Msgs sent/rcvd: 44/46; Downstream
Up time: 00:26:54
LDP discovery sources:
GigabitEthernet0/0, Src IP addr: 10.3.4.4
Addresses bound to peer LDP Ident:
10.3.4.4 4.4.4.4 10.1.4.4
Peer LDP Ident: 2.2.2.2:0; Local LDP Ident 3.3.3.3:0
TCP connection: 2.2.2.2.646 - 3.3.3.3.23943
State: Oper; Msgs sent/rcvd: 45/45; Downstream
Up time: 00:26:51
LDP discovery sources:
GigabitEthernet0/2, Src IP addr: 10.2.3.2
Addresses bound to peer LDP Ident:
10.1.2.2 10.2.5.2 10.2.3.2 2.2.2.2
Peer LDP Ident: 1.1.1.1:0; Local LDP Ident 3.3.3.3:0
TCP connection: 1.1.1.1.646 - 3.3.3.3.22044
State: Oper; Msgs sent/rcvd: 45/45; Downstream
Up time: 00:26:51
LDP discovery sources:
GigabitEthernet0/1, Src IP addr: 10.1.3.1
Addresses bound to peer LDP Ident:
10.1.2.1 10.1.3.1 10.1.4.1 1.1.1.1
Router Configurations
P Routers: (Router1, Router2, Router3)
The P routers are configured with the standard subnetting scheme from the table above in combination with OSPF area 0 and LDP as the labelling protocol. The Label range is based on the Router number.
Router1, Router2, Router2#
#---- MPLS ranges and LDP
#---- Modify label range per router
mpls label range 100 199
mpls label protocol ldp
mpls ldp router-id Loopback0 force
#---- Interface configuration with MPLS & OSPF
interface Loopback0
ip address 1.1.1.1 255.255.255.255
ip ospf 1 area 0
!
interface GigabitEthernet0/0
ip address 10.1.2.1 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
!
interface GigabitEthernet0/1
ip address 10.1.3.1 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
!
interface GigabitEthernet0/3
ip address 10.1.4.1 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
!
PE Routers: (Router4, Router5)
The PE routers are configured with the standard subnetting scheme from the table above in combination with OSPF area 0 and LDP as the labelling protocol.
Each PE routers has an IBGP session to the other PE router (Router4 <-> Router5) for CE traffic.
Router4 (PE)
# ============= MPLS
mpls label range 400 499
mpls label protocol ldp
mpls ldp router-id Loopback0 force
# ===== Interfaces
interface Loopback0
ip address 4.4.4.4 255.255.255.255
ip ospf 1 area 0
!
interface GigabitEthernet0/0
ip address 10.3.4.4 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
!
interface GigabitEthernet0/1
ip vrf forwarding CUST
ip address 10.4.6.4 255.255.255.0
!
interface GigabitEthernet0/3
ip address 10.1.4.4 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
# ============= OSPF
router ospf 1
router-id 4.4.4.4
!
# =========== BGP
router bgp 65000
template peer-session IBGP
remote-as 65000
transport connection-mode active
update-source Loopback0
exit-peer-session
!
bgp router-id 4.4.4.4
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 5.5.5.5 inherit peer-session IBGP
neighbor 5.5.5.5 transport connection-mode passive
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 5.5.5.5 activate
neighbor 5.5.5.5 send-community extended
neighbor 5.5.5.5 next-hop-self
exit-address-family
!
address-family ipv4 vrf CUST
neighbor 10.4.6.6 remote-as 65006
neighbor 10.4.6.6 activate
neighbor 10.4.6.6 as-override
exit-address-familyRouter5 (PE)
# ============= MPLS
mpls label range 500 599
mpls label protocol ldp
mpls ldp router-id Loopback0 force
# ===== Interfaces
interface Loopback0
ip address 5.5.5.5 255.255.255.255
ip ospf 1 area 0
!
interface GigabitEthernet0/1
ip address 10.2.5.5 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
!
interface GigabitEthernet0/2
ip vrf forwarding CUST
ip address 10.5.7.5 255.255.255.0
!
interface GigabitEthernet0/3
ip address 10.3.5.5 255.255.255.0
ip ospf network point-to-point
ip ospf 1 area 0
mpls ip
# ============= OSPF
router ospf 1
router-id 5.5.5.5
!
# =========== BGP
router bgp 65000
template peer-session IBGP
remote-as 65000
transport connection-mode active
update-source Loopback0
exit-peer-session
!
bgp router-id 5.5.5.5
bgp log-neighbor-changes
no bgp default ipv4-unicast
neighbor 4.4.4.4 inherit peer-session IBGP
!
address-family ipv4
exit-address-family
!
address-family vpnv4
neighbor 4.4.4.4 activate
neighbor 4.4.4.4 send-community extended
neighbor 4.4.4.4 next-hop-self
exit-address-family
!
address-family ipv4 vrf CUST
neighbor 10.5.7.7 remote-as 65006
neighbor 10.5.7.7 activate
neighbor 10.5.7.7 as-override
exit-address-familyTraceroute between CE routers before TE (R6->R7)
When performing a traceroute between CE routers we see the default IGP shortest path behaviour.
R6 -> R4 -> R3 -> R5 -> R7.
After MPLS-TE we will have created the following path:
R6 -> R4 -> R1 -> R2 -> R5 -> R7.
Router6#traceroute 7.7.7.7 source 6.6.6.6
Type escape sequence to abort.
Tracing the route to 7.7.7.7
VRF info: (vrf in name/id, vrf out name/id)
1 10.4.6.4 2 msec 3 msec 2 msec
2 10.3.4.3 [MPLS: Labels 303/511 Exp 0] 10 msec 8 msec 7 msec
3 10.5.7.5 [AS 65000] [MPLS: Label 511 Exp 0] 9 msec 8 msec 11 msec
4 10.5.7.7 [AS 65000] 12 msec 12 msec *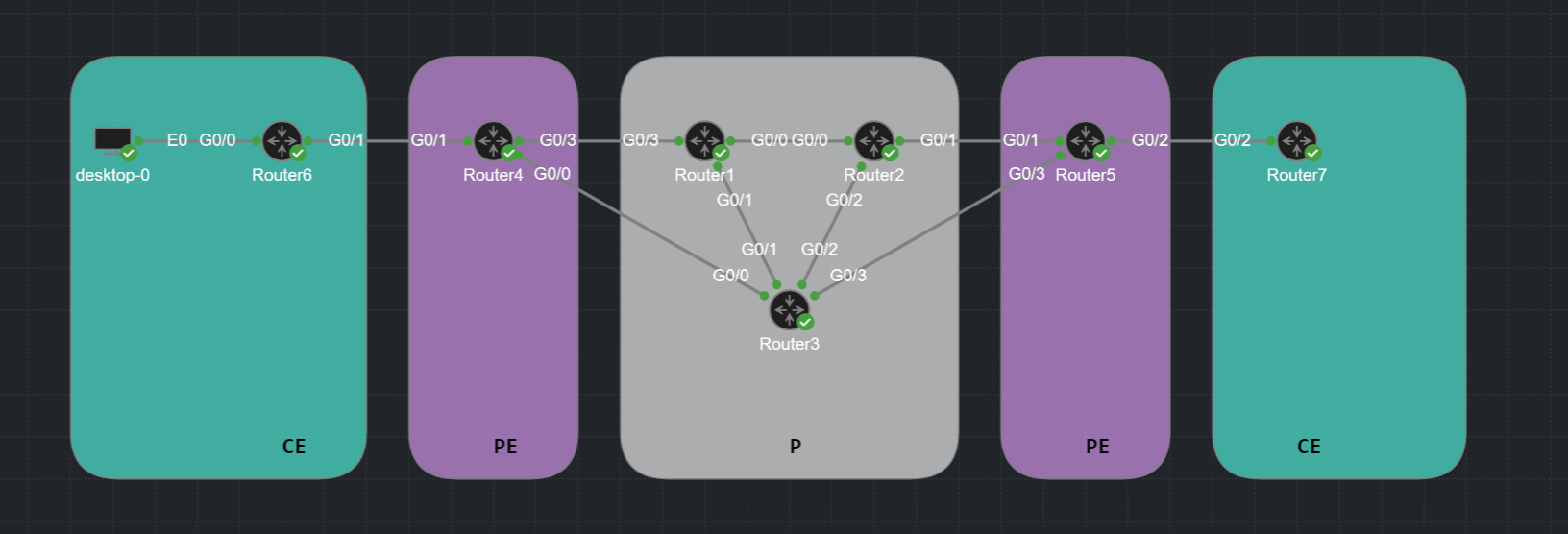

 Last weekend I decided to try Cisco’s Modeling Labs (CML). This is Cisco’s network virtualization platform comparable to GNS3 or EVE-NG. It replaced an older Cisco product called VIRL (Virtual Internet Routing Lab), offering more features and improved performance.
Last weekend I decided to try Cisco’s Modeling Labs (CML). This is Cisco’s network virtualization platform comparable to GNS3 or EVE-NG. It replaced an older Cisco product called VIRL (Virtual Internet Routing Lab), offering more features and improved performance.
 2: Accept the EULA:
2: Accept the EULA: 3: Information for accessing the Cockpit (port 9090):
3: Information for accessing the Cockpit (port 9090): 4: Continue:
4: Continue: 5: Continue with standalone all-in-one deployment.:
5: Continue with standalone all-in-one deployment.: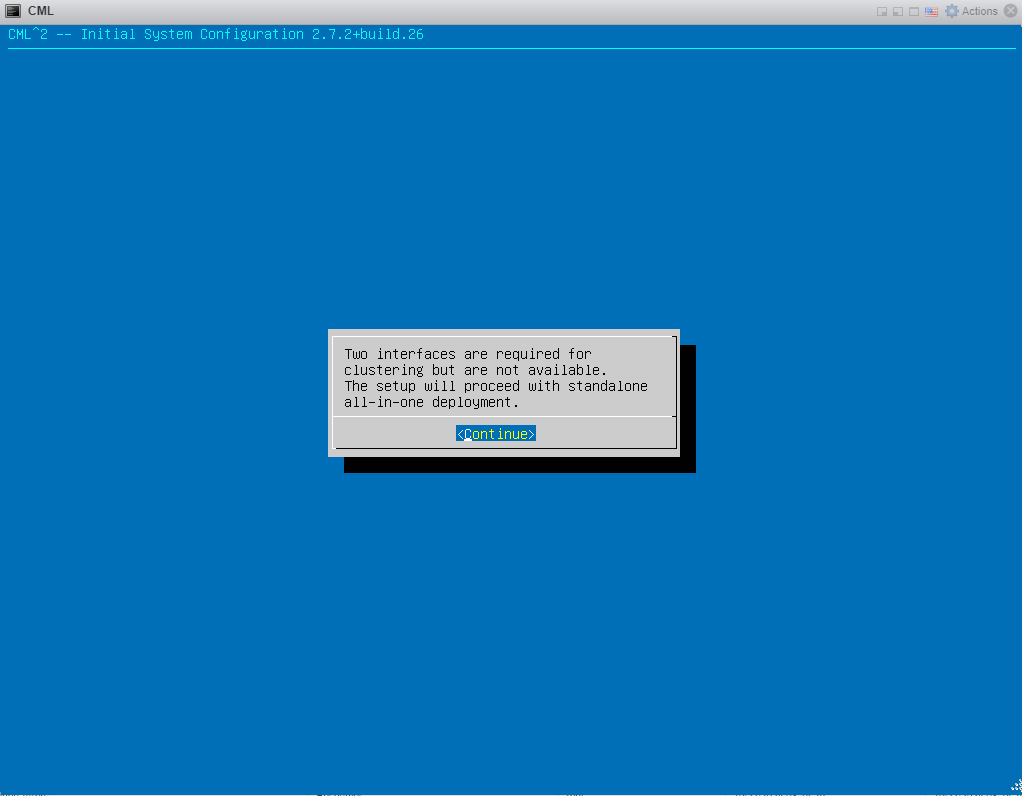 6: Enter the hostname:
6: Enter the hostname: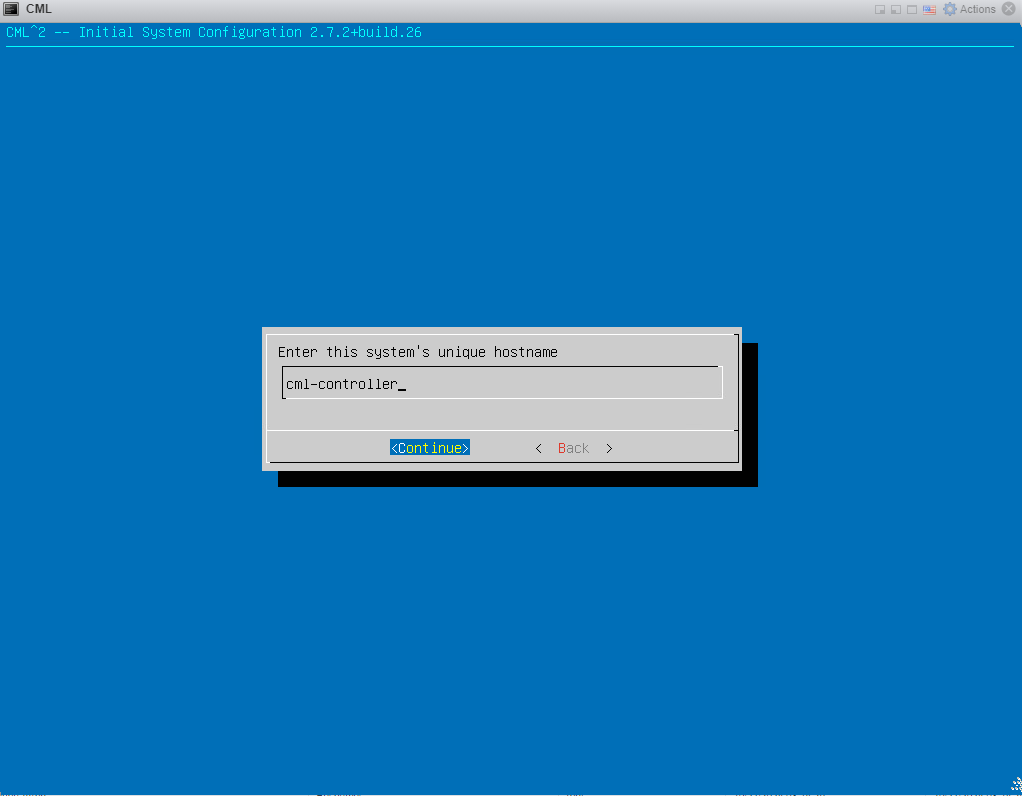 7: Create a system user:
7: Create a system user: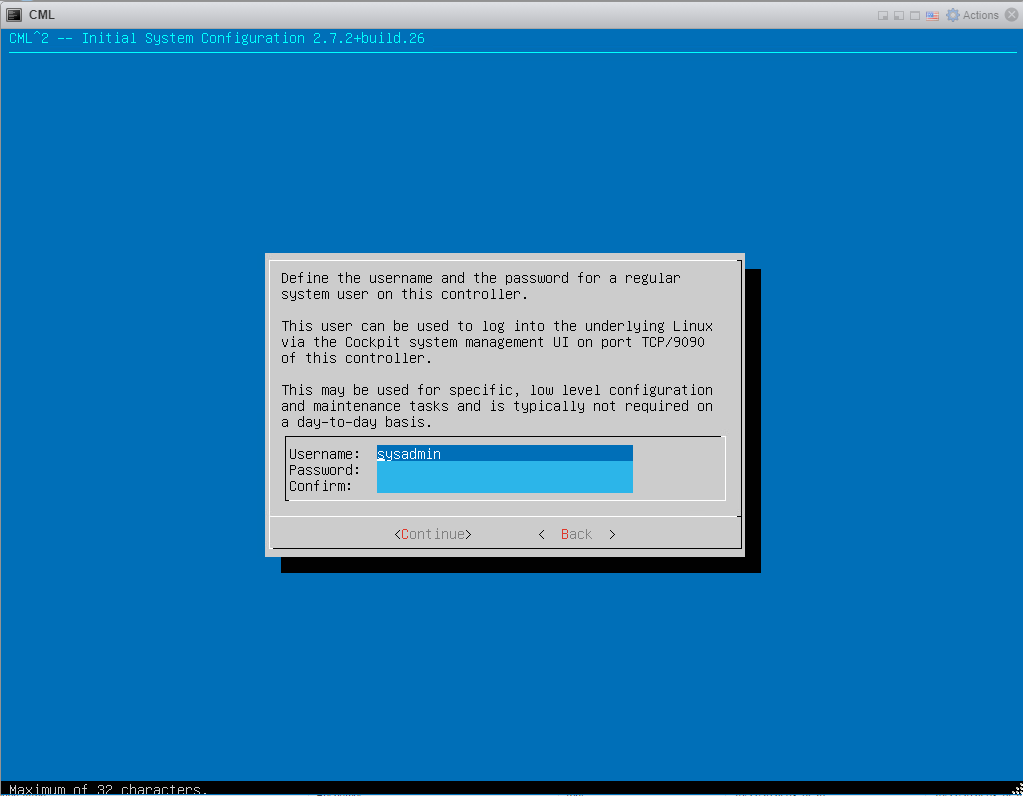 8: Create the admin user:
8: Create the admin user: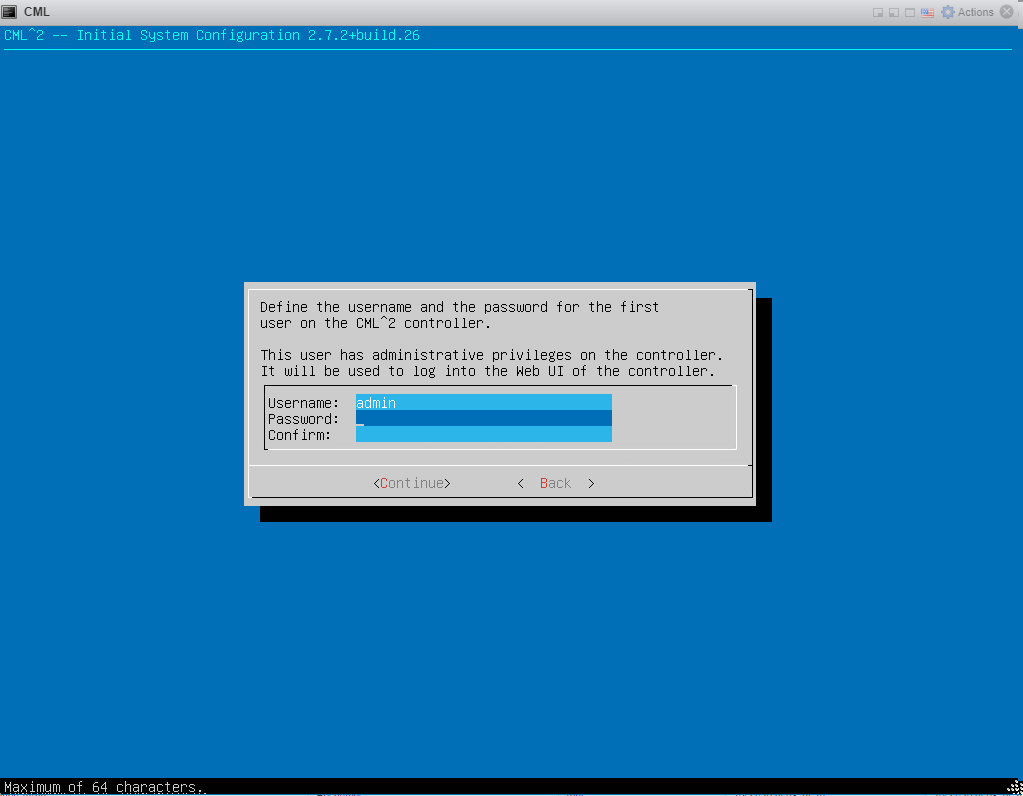 9: IP addressing:
9: IP addressing: